Monday, September 12, 2005
Oracle to buy Siebel for $5.85bn
Oracle is offering $10.66 per Siebel share, 16.8% more than Siebel's closing share price on Friday.
Siebel makes software to help companies manage their relationships with clients. The takeover by Oracle had long been predicted by analysts.
It is the latest acquisition by Oracle which bought another rival, Peoplesoft, in December last year for $10bn.
Board backing
"In a single step, Oracle becomes the number one CRM [customer relationship management] applications company in the world," said Oracle chief executive Larry Ellison.
| | |
"Siebel's 4,000 applications customers and 3.4 million CRM users strengthen our number one position in applications in North America and move us closer to the number one position in applications globally."
Oracle said the deal had the approval of the Siebel board and that the takeover was expected to be completed in 2006, subject to regulatory approval.
It also said that the customers of both firms had long called for them to come together.
Profit target
The purchase of Siebel is likely to help Oracle achieve its stated goal of 20% long-term annual earnings growth.
Software firms analyst Peter Jacobson of Kaufman Brothers said some Siebel shareholders might call for Oracle to pay a higher price, but at the same time he noted that Siebel's performance had not been brilliant in recent times.
"More often than not, these deals go through at agreed-to valuations," said Mr Jacobson.
Shares in Siebel were up 13% in Monday lunchtime trading on the Nasdaq, while Oracle's stock had gained 0.75%.
source:http://newsvote.bbc.co.uk/mpapps/pagetools/print/news.bbc.co.uk/1/hi/business/4237810.stm
iPod nano
Introduction
![]() iPod nano
iPod nano
Manufacturer: Apple (product page)
System requirements: Macintosh computer running Mac OS X 10.3.4 or later, USB port; Windows PC running Windows 2000 SP4 or Windows XP SP2, USB port
Price: US$199 (2GB), US$249 (shop for the iPod nano)
As we all know, Apple's iPod has dominated the digital music player scene since its launch in 2001, much like an aardvark busting through a termite mound. As hard-drive-based players have gotten smaller and the price of flash-based players has dropped, Apple seized on the opportunity to dive into the flash-based market with the iPod shuffle. It was a wildly successful move for Apple, which has grabbed close to 46 percent of the flash-based player market since its inception. However, there were still many reasons for users not to get the shuffle—namely, the lack of a screen and sophisticated controls. The task for Apple was to create a music player that was somehow a marriage between the minute size of the iPod shuffle and the versatility of a regular iPod.
Last Tuesday, Apple's solution came in the form of the iPod nano, a mini-mini-version of their current iPod color line. That's right, it's more miniature than the iPod mini, and the display is color! It's clear that these two superior elements are the reasons why Apple decided to do away with the original iPod mini line; however many consumers are upset that the iPod nano's storage capacity is smaller than what the iPod mini used to be. At 2GB and 4GB, though, the capacities are higher than the current iPod shuffle line and the pricing falls right in line in between shuffles and regular color iPods.
A brief word about sound quality: the iPod nano essentially uses the same sound codec as the regular iPod. It sounds just like any other iPod.
Opening the package
The out-of-box experience was nothing less than expected from Apple: excessive, high-end, and oh-so-delightful. When purchasing our 2GB black iPod nano for this review, it even came in a "commemorative" iPod nano bag.

Opening the slim nano box was pretty much the same as opening any other iPod, and the contents were laid out in a similar manner—simple, elegant, and organized.

It's when you take the iPod nano out of the box that the true experience begins. That thing is really, really nano! Photos don't even convey how small and light the iPod nano really is. In fact at first, at 3.5" x 1.6" x 0.27" and 1.5 ounces, it almost seemed too small and too light for me in my hand. The thinness is marvelous from an aesthetic and engineering standpoint, but my first thought upon holding it was don't break it. We'll get to exploring that thought later, though.
The iPod nano is so thin that it slips effortlessly into the coin pocket on a pair of women's jeans, with room to spare. It certainly makes the "thousand songs right in your pocket" example a reality, especially to women who have very little pocket space and are much more adverse to carrying bulkier electronics in those pockets than men. The iPod nano barely shows a profile in the pocket and it's easy to forget about its presence after carrying it around for awhile.

The iPod nano comes with all of the standard accessories, including the standard white iPod headphones (some people have poined out that providing black iPod nano with white headphones is a bit of a fashion faux pas, but I'll leave that rant for a different time), a USB cable, and a dock adapter for use of your iPod nano with a standard iPod dock. However, the nano's dock adapter must be too complex for us two lowly engineers, because getting it to fit with either of our regular iPod docks was (and still is) truly perplexing. After nearly thirty minutes of fiddling between the two of us, we finally gave up on the nano dock adapter altogether. Worry not, however, as the iPod nano plugs just dandily into a regular dock without the adapter—it just sits straight up in the middle of the designated iPod area instead of being flush with plastic all the way around.
Update: After publishing this review last night, we had several readers contact us with information concerning the so-called "Dock Adapter." Dan Frakes from Playlist Magazine provided us with the most information and it came straight from the marketing folks in attendance at the special event. According to Dan, the "dock adapter" is meant to be to be used with future iPod accessories so that they will be able to connect to practically any new iPod. In a utopian world, this would mean that your new iPod would instantly be compatible with any new accessory that offered support for the "universal dock adapter." See this Apple Knowledge Base article for more info.

Usage
Usage of the iPod nano is exactly the same as using any of the hard-drive-based iPods. The click wheel is solid state and touch sensitive, but the various buttons on all sides of the wheel depress slightly when pressing them, giving the user that oh-so-necessary force feedback. The user interface is also the same as you would expect to find on the current iPod color line, but with three new and very interesting features.
The first new feature is the addition of world clocks. Only available on the iPod nano, you can now set however many clocks you'd like in various cities around the world and then see the time in multiple locations at a glance. Seemingly trivial but surprisingly helpful is the fact that the clocks turn black when it is night time in that particular locale while remaining white during the daytime in another locale, which makes for even easier interpretation of the times. You can also set alarms in various time zones, set the clocks to change at Daylight Saving Time (or not, if you're into that sort of thing) and sleep timers in different cities.


The second new feature is the Stopwatch. You can now press a button and start using the iPod nano just as you would a regular stopwatch, with the ability to pause and even hit the "Lap" button to keep stats for each lap. When finished, you can look at the stats of your stopwatch session and if you had been keeping track of laps, the iPod nano shows you statistics for your laps such as your best lap time. The nano saves your stopwatch stats for multiple sessions, even after you exit the stopwatch on the nano, which can be useful for recording data for multiple people or multiple sessions of your own and then analyzing the data at a later time.

Finally, the last new nano feature is the presence of the Screen Lock. We're not 100% clear on what the purpose of this is, ourselves, but interesting nonetheless. There is a preferences screen where you can set the code for your screen lock, and another screen where you lock it. Once the iPod nano is "screen locked," no one can access anything on it unless they enter the correct code via a graphical combination lock that you turn by, you guessed it, running your thumb around the iPod wheel like you would to scroll through songs. This seems a little bit excessive and unnecessary, but it's cute and does the job. (Sounds just like something Apple would do.)


It's interesting to note, by the way, that both the Stopwatch and the Screen Lock both made use of the brushed metal that seems to have conveniently disappeared from iTunes 5.
Since the iPod's interface is nearly identical to the regular iPod's (save the three nano-only new features), it seems unnecessary to go into detail about how it works. However, the nano being our first iPod that has photo capabilities, we'd like to quickly go over how that part of it functions with the computer.
In order to transfer photos to the iPod on the Mac, you can do so in the exact same way that you do for music through iTunes. If you have the iPod nano plugged into the computer via USB and go into the iPod preferences in iTunes, there is a tab for music where you select whether you want to automatically update all songs, update certain playlists, or manually update. Very similarly, there is a "photos" tab that functions in exactly the same manner, except pulling your photo albums from iPhoto.
There, you can select whether you want all photos to update to the iPod, update only certain albums, or update manually. After iTunes has finished updating songs and photos on your iPod, you can unplug it and view the photos on the iPod by selecting the "Photos" menu and then selecting the album name you want to view. You can then see little thumbnails and scroll through to select one to view, or select the first one and hit back/next to view the ones before and after it. You can also scroll through the photos at "full" size with the volume wheel.
As we conclude the discussion of the photo capabilities, we'd like to point out that using the photo feature on the iPod nano seems somewhat pointless due to the smallness of the screen. It felt a little like looking at postage-stamp-sized photos on your cell phone, except our cell phones actually have larger screens than the iPod nano and the photos were higher resolution than photos taken from a camera phone. Although it's a nice extra feature to have on the iPod nano, the photo element is probably better used and appreciated on a full-size iPod.
Stress testing
What does it take to destroy an iPod nano, and what's inside this tiny package? We wanted to answer both questions and strangely enough answering the first allowed us to answer the second. We could take our turns at purposely rendering the iPod nano broken, and then when it had endured more damage than it could handle we'd end its misery with a respectful autopsy. Now, we know that destroying the iPod nano makes some (strange) grown men want to cry. Rest assured, you can still buy one yourself, and the local priest said all iPod nanos go to heaven.
Because of our initial apprehension about the breakability of our tiny new friend as well as reading about similar apprehension from many potential iPod nano buyers online, we decided to abuse our precious little nano for the sake of science. We wanted to stress test the nano in various real-life situations where iPod users have proven themselves to be a little less than genius in the past to see how the nano could handle the abuse. To break the nano in the most scientific manner possible, we would need 5 or 6 nanos and a high-tech laboratory built for this purpose. Unfortunately, all we had was a single 2GB black iPod nano and a giant parking lot, so we had to make do. What we get is a great idea of how much abuse this little guy can take.
To simulate everyday accidents that could result in a broken iPod, we came up with a few situations that we felt would ultimately leave the nano lifeless:
- Sitting on the iPod nano
- Dropping it while jogging (4-6mph),
- Dropping at various speeds: 8-10mph (slow bicycle), 15-20mph (fast bicycle), 30mph (slow car), and 50mph (fast car)
- Dropping the nano from various heights.
Our first test consisted of placing the iPod nano on a solid wood chair and sitting on it, as people are prone to do from time to time. As you can guess, this "test" yielded basically zero damage results—so little, in fact, that we didn't even take pictures.
For our second test, one of us held on to the iPod, jogged about 20 feet and dropped the nano onto a sidewalk. This proved pretty uneventful as well and the nano didn't even skip a beat:

Then, one of us jumped in the car and we started on the higher-speed tests. We drove a slow 10mph around a tiny roundabout and released the nano out of the driver's side window. The nano didn't really slide that much and just fell the to ground. The results for the "slow bicycle" test were duplicated for the "fast bicycle" test. The nano didn't slide much and again, just fell to the ground with some slight scratches.
The nano was still working fine, so we took it up to 30mph and performed the same drop. This time it slid pretty far and surprisingly endured only cosmetic scratches, mostly on the front of the player:

Because of the distinct lack of expected damage from the first two car drops, we sped up to 50mph and launched the nano on an impressive slide and tumble that, again, really only scratched the surface:


Next we tried dropping it from a "considerable" height. The height we dropped it from was approximately 9ft (ie. one of us standing on a stone bench at the park). This was the first point where the iPod started to operate abnormally. The display was seriously bugged out, but the music continued to play and navigating via the scroll wheel still worked as expected:


At this point we were astounded that the iPod nano was still working properly, albeit with a broken display. Because we had honestly expected the iPod nano to break by this time, we were forced to depart from our planned schedule of destruction and try and run over it with the car. Surely, we thought, it could never withstand the crushing power of German automotive engineering.

We placed the nano in the path of the car and drove over it with both front and rear tires. Driving over the nano produced sickening crunching noises which coincidentally sounded a lot like an LCD being crushed. After the first hit and run, the iPod's display was not cracked but was showing some nasty vertical lines. Shockingly, the nano was still playing music and the controls still operated as expected, as we were still able to skip ahead, go back, pause, and play music!


What were we to do now? Baffled, we did the only thing we could think of at the time: we ran over the nano again! This time the screen went totally blank, but the band played on.
In a final act of desperation, we decided to expose the iPod to a catastrophic event that would certainly destroy it. Lacking a really high place to drop the nano from, we decided the throw the nano as high as we could, say 40 feet into the air, and let it land—hard—on the concrete.


Alas, the iPod nano finally gave up the ghost. In addition to the display showing nothing and the backlight being perpetually stuck on, the music finally subsided. The nano had journeyed to the Land Where Consumer Electronics Are Eternally Blessed.


It's dead, Jim.
Since it was dead, we thought we'd open it up and see what made it tick...
Autopsy
With the iPod nano dead, we were ready to figure out what made it tick while it lived. Fortunately for us, the case was very nearly popping open from all the abuse, which made getting inside a snap. When we got home, we tore into the casing which was held together with a bunch of metal clips attached to the polished metal back.
The first thing you'll notice with the rear case removed is the "speaker" that's integrated into it. When the case is completely closed, the speaker touches two contacts on the flat speaker, which produces the clicker noise.

Removing the circuit board from the front part of the case is a bit more difficult due to the copious amounts of sticky glue-like substance (glue?) used to secure it in place. There are also a number of white plastic clips on the LCD assembly that attach to the main board and hold it into place.
With the main board removed, you notice a few things. The scroll wheel and LCD attach via some Foxcomm connectors whereas the battery is soldered directly to to the board:

Next, we removed the LCD and scroll wheel from the board and took a moment to admire the amazing engineering that must've gone into this device.

The first thing we noticed was that this 2GB version's internals were somewhat different from the 4GB disassembles we saw online a few days ago. Apparently in the 4GB version, instead of soldering the memory directly to the board, they soldered it to a daughter board which attaches via some sort of connector. In fact, on the 2GB version, the base circuitry for the daughter board is in place, with only the connector missing:

Also interesting is the use of Toshiba memory chips on the 2GB model instead of Samsung chips on the 4GB model. It was announced earlier this month that Apple would be snatching up nearly 40% of Samsung's entire output for upcoming products. Was Samsung's contribution still not enough to feed Apple iPod production? For whatever reason, Apple is not using Samsung's flash memory on its 2GB models for the time being.
The specific chips being used are Toshiba 1GB, model number TH58NVG3D4BTG00. They don't appear to be listed on Toshiba's website, but these chips are somewhat similar.

Another interesting design choice was to move away from Synaptics as the supplier of the touch-sensitive wheel. From our inspection of the circuitry of the touch wheel on the iPod nano, it appears that Apple has designed this one from scratch. In fact, our Apple journal, Infinite Loop even pointed to a report by AppleInsider that talked about just this sort of shift in Apple's quest to shave costs:
The iPod's navigational controls will be one of the first components to see such changes, sources have told AppleInsider. By October, Apple is expected to abandon Synaptics as its supplier of iPod scroll-wheels for its white iPods in favor of an in-house solution.
While AI was off the mark about the exact nature of the iPod models, they were dead on about the shift in technology. Apple's new touch pad has integrated membrane-style momentary switches and is controlled by a Cypress CY8C21424 Mixed-Signal Array with On-Chip Controller.


Most of the other components are run of the mill as far as iPods go. The heart of the iPod, the PortalPlayer chip, was upgraded to a slightly newer model (the PP5021C-TDF), the audio codec is the same Wolfson Microprocessor (WM8975G) found in the current generation iPods, a new power management unit by Phillips (CF50607), a batch of 32MB of Samsung SDRAM (534-K9WAG08U1M) replaces the old Hynix chips, and the LCD is of unknown manufacturer but it's a 16-bit color, 176x132 1.5" model.
Conclusion
The iPod nano is clearly intended to be Apple's new best-selling iPod product, as the iPod mini used to hold that title but no longer exists. And honestly, given all of the improvements that the iPod nano has seen over the mini and even regular-sized iPods, we can see it hitting that point in the very near future as Christmas decorations start showing up in stores sometime in mid-October.
Diehard iPod users who have gigs upon gigs of music will probably still avoid the nano because of its relatively small storage capacity in comparison with standard iPods. After all, the gap between the highest-end iPod nano and the lowest-end iPod is rather large—4GB vs. 20GB—but of course, with only a US$50 difference between the two, this strategic spacing is right out of Apple's playbook. However, iPod shuffle users and previous (or even current) iPod mini users may be very tempted to get an iPod nano now, given all of the new and shrunken bright & shiny features.
 Or, if you're like us, you're one of Apple's most favorite customers of all: iPod adders. No matter what you already have, you'll want to add an iPod nano to your collection.
Or, if you're like us, you're one of Apple's most favorite customers of all: iPod adders. No matter what you already have, you'll want to add an iPod nano to your collection.
The nano is nearly perfect; it is amazingly small and packs almost all of the features of the iPod photo and a few more. If it weren't for its lack of Firewire, lack of compatibility with older accessories, and no current support for video output, I don't think we'd hesitate to give the nano a perfect ten. Those shortcomings drop the iPod nano's score a couple of points to a solid eight.
Pros:- Very light and tiny, sits very easily in hand and pocket
- Extremely durable
- Cool new nano-only features (screen lock, world clock, stop watch)
- US$200 for 2GB iPod with a color screen and all the bells and whistles is a good deal compared to US$130 1GB iPod shuffle.
- Great battery life (14hrs)
- Charges over USB
- Tiny screen means it's hard to enjoy looking at photos
- Smaller storage capacities than the iPod mini it replaced
- Transfer over Firewire not allowed—USB only
- Dock adapter, wtf?
- No AV output
- No remote
- Incompatible with mini and normal iPod accessories that require the remote connector.
- Battery is soldered in
source:http://arstechnica.com/reviews/hardware/nano.ars/1
eBay to buy Skype in $2.6bn deal
eBay said it would pay half the amount in cash and the other half in stocks to create "an unparalleled e-commerce and communications engine".
Skype's software lets PC users talk to each other for free and make cut-price calls to mobiles and landlines.
Other players in the online phone market include computer giants such as Google, Microsoft, AOL and Yahoo.
Google recently launched its Talk service, while Microsoft purchased leading player Teleo for an undisclosed sum.
Technology used by Skype, and rivals such as Vonage, converts phone conversations into packets of data and transmits them down the same wires used to surf the internet.
'Powerful environment'
"Communications is at the heart of e-commerce and community," said eBay chief executive Meg Whitman.
| | |
The company said the move would "strengthen eBay's global marketplace and payments platform, while opening several new lines of business".
Skype chief executive Niklas Zennstrom, who will join eBay's senior management team, said the deal would help "revolutionise the ease with which people can communicate through the internet".
Using Voice over Internet Protocol (VoIP) services, computer users can talk to each other via a headset or microphone and speakers.
Cheap calls to landlines and mobile phones are also possible. Some systems allow users to plug their traditional phones into a desktop box that allows them to make VoIP calls.
Growth market?
Skype has 53 million registered users and says more than two million people are using its software at any given moment.
Since it was introduced in 2003, the free program has been downloaded more than 151 million times.
The company does not release earnings figures.
Vonage, the largest internet phone company, has nearly one million subscribers who pay a monthly fee of $25 to use it.
eBay has been buying up firms - including payment system PayPal - in an effort to increase the number of services it offers consumers and keep its profits growing.
Media reports have speculated that as well as looking to tap into the growing internet phone market, eBay is also attracted by the idea of letting its buyers and sellers talk to each other via their computers.
source: http://newsvote.bbc.co.uk/mpapps/pagetools/print/news.bbc.co.uk/2/hi/business/4237338.stm
The Six Dumbest Ideas in Computer Security
There's lots of innovation going on in security - we're inundated with a steady stream of new stuff and it all sounds like it works just great. Every couple of months I'm invited to a new computer security conference, or I'm asked to write a foreword for a new computer security book. And, thanks to the fact that it's a topic of public concern and a "safe issue" for politicians, we can expect a flood of computer security-related legislation from lawmakers. So: computer security is definitely still a "hot topic." But why are we spending all this time and money and still having problems?
Let me introduce you to the six dumbest ideas in computer security. What are they? They're the anti-good ideas. They're the braindamage that makes your $100,000 ASIC-based turbo-stateful packet-mulching firewall transparent to hackers. Where do anti-good ideas come from? They come from misguided attempts to do the impossible - which is another way of saying "trying to ignore reality." Frequently those misguided attempts are sincere efforts by well-meaning people or companies who just don't fully understand the situation, but other times it's just a bunch of savvy entrepreneurs with a well-marketed piece of junk they're selling to make a fast buck. In either case, these dumb ideas are the fundamental reason(s) why all that money you spend on information security is going to be wasted, unless you somehow manage to avoid them.
For your convenience, I've listed the dumb ideas in descending order from the most-frequently-seen. If you can avoid falling into the the trap of the first three, you're among the few true computer security elite.
#1) Default Permit
This dumb idea crops up in a lot of different forms; it's incredibly persistent and difficult to eradicate. Why? Because it's so attractive. Systems based on "Default Permit" are the computer security equivalent of empty calories: tasty, yet fattening.
The most recognizable form in which the "Default Permit" dumb idea manifests itself is in firewall rules. Back in the very early days of computer security, network managers would set up an internet connection and decide to secure it by turning off incoming telnet, incoming rlogin, and incoming FTP. Everything else was allowed through, hence the name "Default Permit." This put the security practitioner in an endless arms-race with the hackers. Suppose a new vulnerability is found in a service that is not blocked - now the administrators need to decide whether to deny it or not, hopefully, before they got hacked. A lot of organizations adopted "Default Permit" in the early 1990's and convinced themselves it was OK because "hackers will never bother to come after us." The 1990's, with the advent of worms, should have killed off "Default Permit" forever but it didn't. In fact, most networks today are still built around the notion of an open core with no segmentation. That's "Default Permit."
Another place where "Default Permit" crops up is in how we typically approach code execution on our systems. The default is to permit anything on your machine to execute if you click on it, unless its execution is denied by something like an antivirus program or a spyware blocker. If you think about that for a few seconds, you'll realize what a dumb idea that is. On my computer here I run about 15 different applications on a regular basis. There are probably another 20 or 30 installed that I use every couple of months or so. I still don't understand why operating systems are so dumb that they let any old virus or piece of spyware execute without even asking me. That's "Default Permit."
A few years ago I worked on analyzing a website's security posture as part of an E-banking security project. The website had a load-balancer in front of it, that was capable of re-vectoring traffic by URL, and my client wanted to use the load-balancer to deflect worms and hackers by re-vectoring attacks to a black hole address. Re-vectoring attacks would have meant adopting a policy of "Default Permit" (i.e.: if it's not a known attack, let it through) but instead I talked them into adopting the opposite approach. The load-balancer was configured to re-vector any traffic not matching a complete list of correctly-structured URLs to a server that serves up image data and 404 pages, which is running a special locked-down configuration. Not surprisingly, that site has withstood the test of time quite well.
One clear symptom that you've got a case of "Default Permit" is when you find yourself in an arms race with the hackers. It means that you've put yourself in a situation where what you don't know can hurt you, and you'll be doomed to playing keep ahead/catch-up.
The opposite of "Default Permit" is "Default Deny" and it is a really good idea. It takes dedication, thought, and understanding to implement a "Default Deny" policy, which is why it is so seldom done. It's not that much harder to do than "Default Permit" but you'll sleep much better at night.
#2) Enumerating Badness
Back in the early days of computer security, there were only a relatively small number of well-known security holes. That had a lot to do with the widespread adoption of "Default Permit" because, when there were only 15 well-known ways to hack into a network, it was possible to individually examine and think about those 15 attack vectors and block them. So security practitioners got into the habit of "Enumerating Badness" - listing all the bad things that we know about. Once you list all the badness, then you can put things in place to detect it, or block it.
Figure 1: The "Badness Gap"

Why is "Enumerating Badness" a dumb idea? It's a dumb idea because sometime around 1992 the amount of Badness in the Internet began to vastly outweigh the amount of Goodness. For every harmless, legitimate, application, there are dozens or hundreds of pieces of malware, worm tests, exploits, or viral code. Examine a typical antivirus package and you'll see it knows about 75,000+ viruses that might infect your machine. Compare that to the legitimate 30 or so apps that I've installed on my machine, and you can see it's rather dumb to try to track 75,000 pieces of Badness when even a simpleton could track 30 pieces of Goodness. In fact, if I were to simply track the 30 pieces of Goodness on my machine, and allow nothing else to run, I would have simultaneously solved the following problems:
- Spyware
- Viruses
- Remote Control Trojans
- Exploits that involve executing pre-installed code that you don't use regularly
Thanks to all the marketing hype around disclosing and announcing vulnerabilities, there are (according to some industry analysts) between 200 and 700 new pieces of Badness hitting the Internet every month. Not only is "Enumerating Badness" a dumb idea, it's gotten dumber during the few minutes of your time you've bequeathed me by reading this article.
Now, your typical IT executive, when I discuss this concept with him or her, will stand up and say something like, "That sounds great, but our enterprise network is really complicated. Knowing about all the different apps that we rely on would be impossible! What you're saying sounds reasonable until you think about it and realize how absurd it is!" To which I respond, "What about the title 'Chief Technology Officer' are you earning if you don't know what your systems are running and/or being used for?"
In 1994 I wrote a firewall product that needed some system log analysis routines that would alert the administrator in case some kind of unexpected condition was detected. The first version used "Enumerating Badness" (I've been dumb, too) but the second version used what I termed "Artificial Ignorance" - a process whereby you throw away the log entries you know aren't interesting. If there's anything left after you've thrown away the stuff you know isn't interesting, then the leftovers must be interesting. This approach worked amazingly well, and detected a number of very interesting operational conditions and errors that it simply never would have occurred to me to look for.
"Enumerating Badness" is the idea behind a huge number of security products and systems, from anti-virus to intrusion detection, intrusion prevention, application security, and "deep packet inspection" firewalls. What these programs and devices do is outsource your process of knowing what's good. Instead of you taking the time to list the 30 or so legitimate things you need to do, it's easier to pay $29.95/year to someone else who will try to maintain an exhaustive list of all the evil in the world. Except, unfortunately, your badness expert will get $29.95/year for the antivirus list, another $29.95/year for the spyware list, and you'll buy a $19.95 "personal firewall" that has application control for network applications. By the time you're done paying other people to enumerate all the malware your system could come in contact with, you'll more than double the cost of your "inexpensive" desktop operating system.
One clear symptom that you have a case of "Enumerating Badness" is that you've got a system or software that needs signature updates on a regular basis, or a system that lets past a new worm that it hasn't seen before. The cure for "Enumerating Badness" is, of course, "Enumerating Goodness." Amazingly, there is virtually no support in operating systems for such software-level controls. I've tried using Windows XP Pro's Program Execution Control but it's oriented toward "Enumerating Badness" and is, itself a dumb implementation of a dumb idea.
In a sense, "Enumerating Badness" is a special dumb-case of "Default Permit" - our #1 dumb computer security idea. But it's so prevalent that it's in a class by itself.
#3) Penetrate and Patch
There's an old saying, "You cannot make a silk purse out of a sow's ear." It's pretty much true, unless you wind up using so much silk to patch the sow's ear that eventually the sow's ear is completely replaced with silk. Unfortunately, when buggy software is fixed it is almost always fixed through the addition of new code, rather than the removal of old bits of sow's ear.
"Penetrate and Patch" is a dumb idea best expressed in the BASIC programming language:
10 GOSUB LOOK_FOR_HOLES
20 IF HOLE_FOUND = FALSE THEN GOTO 50
30 GOSUB FIX_HOLE
40 GOTO 10
50 GOSUB CONGRATULATE_SELF
60 GOSUB GET_HACKED_EVENTUALLY_ANYWAY
70 GOTO 10In other words, you attack your firewall/software/website/whatever from the outside, identify a flaw in it, fix the flaw, and then go back to looking. One of my programmer buddies refers to this process as "turd polishing" because, as he says, it doesn't make your code any less smelly in the long run but management might enjoy its improved, shiny, appearance in the short term. In other words, the problem with "Penetrate and Patch" is not that it makes your code/implementation/system better by design, rather it merely makes it toughened by trial and error. Richard Fenyman's "Personal Observations on the Reliability of the Space Shuttle" used to be required reading for the software engineers that I hired. It contains some profound thoughts on expectation of reliability and how it is achieved in complex systems. In a nutshell its meaning to programmers is: "Unless your system was supposed to be hackable then it shouldn't be hackable."
"Penetrate and Patch" crops up all over the place, and is the primary dumb idea behind the current fad (which has been going on for about 10 years) of vulnerability disclosure and patch updates. The premise of the "vulnerability researchers" is that they are helping the community by finding holes in software and getting them fixed before the hackers find them and exploit them. The premise of the vendors is that they are doing the right thing by pushing out patches to fix the bugs before the hackers and worm-writers can act upon them. Both parties, in this scenario, are being dumb because if the vendors were writing code that had been designed to be secure and reliable then vulnerability discovery would be a tedious and unrewarding game, indeed!
Let me put it to you in different terms: if "Penetrate and Patch" was effective, we would have run out of security bugs in Internet Explorer by now. What has it been? 2 or 3 a month for 10 years? If you look at major internet applications you'll find that there are a number that consistently have problems with security vulnerabilities. There are also a handful, like PostFix, Qmail, etc, that were engineered to be compartmented against themselves, with modularized permissions and processing, and - not surprisingly - they have histories of amazingly few bugs. The same logic applies to "penetration testing." There are networks that I know of which have been "penetration tested" any number of times and are continually getting hacked to pieces. That's because their design (or their security practices) are so fundamentally flawed that no amount of turd polish is going to keep the hackers out. It just keeps managers and auditors off of the network administrator's backs. I know other networks that it is, literally, pointless to "penetration test" because they were designed from the ground up to be permeable only in certain directions and only to certain traffic destined to carefully configured servers running carefully secured software. Running a "penetration test" for Apache bugs is completely pointless against a server that is running a custom piece of C code that is running in a locked-down portion of an embedded system. So, "Penetrate and Patch" is pointless either because you know you're going to find an endless litany of bugs, or because you know you're not going to find anything comprehensible. Pointless is dumb.
One clear symptom that you've got a case of "Penetrate and Patch " is when you find that your system is always vulnerable to the "bug of the week." It means that you've put yourself in a situation where every time the hackers invent a new weapon, it works against you. Doesn't that sound dumb? Your software and systems should be secure by design and should have been designed with flaw-handling in mind.
#4) Hacking is Cool
One of the best ways to get rid of cockroaches in your kitchen is to scatter bread-crumbs under the stove, right? Wrong! That's a dumb idea. One of the best ways to discourage hacking on the Internet is to give the hackers stock options, buy the books they write about their exploits, take classes on "extreme hacking kung fu" and pay them tens of thousands of dollars to do "penetration tests" against your systems, right? Wrong! "Hacking is Cool" is a really dumb idea.
Around the time I was learning to walk, Donn Parker was researching the behavioral aspects of hacking and computer security. He says it better than I ever could:
"Remote computing freed criminals from the historic requirement of proximity to their crimes. Anonymity and freedom from personal victim confrontation increased the emotional ease of crime, i.e., the victim was only an inanimate computer, not a real person or enterprise. Timid people could become criminals. The proliferation of identical systems and means of use and the automation of business made possible and improved the economics of automating crimes and constructing powerful criminal tools and scripts with great leverage."Hidden in Parker's observation is the awareness that hacking is a social problem. It's not a technology problem, at all. "Timid people could become criminals." The Internet has given a whole new form of elbow-room to the badly socialized borderline personality. The #4th dumbest thing information security practitioners can do is implicitly encourage hackers by lionizing them. The media plays directly into this, by portraying hackers, variously, as "whiz kids" and "brilliant technologists" - of course if you're a reporter for CNN, anyone who can install Linux probably does qualify as a "brilliant technologist" to you. I find it interesting to compare societal reactions to hackers as "whiz kids" versus spammers as "sleazy con artists." I'm actually heartened to see that the spammers, phishers, and other scammers are adopting the hackers and the techniques of the hackers - this will do more to reverse society's view of hacking than any other thing we could do.
If you're a security practitioner, teaching yourself how to hack is also part of the "Hacking is Cool" dumb idea. Think about it for a couple of minutes: teaching yourself a bunch of exploits and how to use them means you're investing your time in learning a bunch of tools and techniques that are going to go stale as soon as everyone has patched that particular hole. It means you've made part of your professional skill-set dependent on "Penetrate and Patch" and you're going to have to be part of the arms-race if you want that skill-set to remain relevant and up-to-date. Wouldn't it be more sensible to learn how to design security systems that are hack-proof than to learn how to identify security systems that are dumb?
My prediction is that the "Hacking is Cool" dumb idea will be a dead idea in the next 10 years. I'd like to fantasize that it will be replaced with its opposite idea, "Good Engineering is Cool" but so far there is no sign that's likely to happen.
#5) Educating Users
"Penetrate and Patch" can be applied to human beings, as well as software, in the form of user education. On the surface of things, the idea of "Educating Users" seems less than dumb: education is always good. On the other hand, like "Penetrate and Patch" if it was going to work, it would have worked by now. There have been numerous interesting studies that indicate that a significant percentage of users will trade their password for a candy bar, and the Anna Kournikova worm showed us that nearly 1/2 of humanity will click on anything purporting to contain nude pictures of semi-famous females. If "Educating Users" is the strategy you plan to embark upon, you should expect to have to "patch" your users every week. That's dumb.
The real question to ask is not "can we educate our users to be better at security?" it is "why do we need to educate our users at all?" In a sense, this is another special case of "Default Permit" - why are users getting executable attachments at all? Why are users expecting to get E-mails from banks where they don't have accounts? Most of the problems that are addressable through user education are self-correcting over time. As a younger generation of workers moves into the workforce, they will come pre-installed with a healthy skepticism about phishing and social engineering.
Dealing with things like attachments and phishing is another case of "Default Permit" - our favorite dumb idea. After all, if you're letting all of your users get attachments in their E-mail you're "Default Permit"ing anything that gets sent to them. A better idea might be to simply quarantine all attachments as they come into the enterprise, delete all the executables outright, and store the few file types you decide are acceptable on a staging server where users can log in with an SSL-enabled browser (requiring a password will quash a lot of worm propagation mechanisms right away) and pull them down. There are freeware tools like MIMEDefang that can be easily harnessed to strip attachments from incoming E-mails, write them to a per-user directory, and replace the attachment in the E-mail message with a URL to the stripped attachment. Why educate your users how to cope with a problem if you can just drive a stake through the problem's heart?
When I was CEO of a small computer security start-up we didn't have a Windows system administrator. All of the employees who wanted to run Windows had to know how to install it and manage it themselves, or they didn't get hired in the first place. My prediction is that in 10 years users that need education will be out of the high-tech workforce entirely, or will be self-training at home in order to stay competitive in the job market. My guess is that this will extend to knowing not to open weird attachments from strangers.
#6) Action is Better Than Inaction
IT executives seem to break down into two categories: the "early adopters" and the "pause and thinkers." Over the course of my career, I've noticed that dramatically fewer of the "early adopters" build successful, secure, mission-critical systems. This is because they somehow believe that "Action is Better Than Inaction" - i.e.: if there's a new whizzbang, it's better to install it right now than to wait, think about it, watch what happens to the other early adopters, and then deploy the technology once it's fully sorted-out and has had its first generation of experienced users. I know one senior IT executive - one of the "pause and thinkers" whose plan for doing a wireless roll-out for their corporate network was "wait 2 years and hire a guy who did a successful wireless deployment for a company larger than us." Not only will the technology be more sorted-out by then, it'll be much, much cheaper. What an utterly brilliant strategy!
There's an important corollary to the "Action is Better Than Inaction" dumb idea, and it's that:
"It is often easier to not do something dumb than it is to do something smart."
Sun Tzu didn't really write that in "The Art of War" but if you tell IT executives that he did, they'll take you much more seriously when you counsel a judicious, thoughtful approach to fielding some new whizzbang. To many of my clients, I have been counselling, "hold off on outsourcing your security for a year or two and then get recommendations and opinions from the bloody, battered survivors - if there are any."You can see the "Action is Better Than Inaction" dumb idea all over corporate networks and it tends to correlate with senior IT managers that make their product-purchasing decisions by reading Gartner research reports and product glossies from vendors. If you find yourself in the chain of command of such a manager, I sincerely hope you've enjoyed this article because you're probably far better acquainted with dumbness than I am.
One extremely useful piece of management kung-fu to remember, if you find yourself up against an "early adopter" is to rely on your peers. Several years ago I had a client who was preparing to spend a ton of money on a technology without testing it operationally. I suggested offhandedly to the senior IT manager in charge that he should send one of his team to a relevant conference (in this case, LISA) where it was likely that someone with hands-on experience with the technology would be in attendance. I proposed that the manager have his employee put a message on the "meet and greet" bulletin board that read:
"Do you have hands-on experience with xyz from pdq.com? If so, I'm authorized to take you to dinner at Ruth's Chris if you promise to give me the low-down on the product off the record. Contact, etc..." The IT manager later told me that a $200 dinner expense saved them over $400,000 worth of hellish technological trauma.It really is easier to not do something dumb than it is to do something smart. The trick is, when you avoid doing something dumb, to make sure your superiors know you navigated around a particularly nasty sand-bar and that you get appropriate credit for being smart. Isn't that the ultimate expression of professional kung-fu? To get credit for not doing anything?!
The Minor Dumbs
These dumb ideas didn't quite merit status as "The Dumbest" ideas in computer security, but they're pretty dumb and deserve mention in passing:
- "We're Not a Target" - yes, you are. Worms aren't smart enough to realize that your web site/home network isn't interesting.
- "Everyone would be secure if they all just ran
" - no, they wouldn't. Operating systems have security problems because they are complex and system administration is not a solved problem in computing. Until someone manages to solve system administration, switching to the flavor-of-the-month is going to be more damaging because you're making it harder for your system administrators to gain a level of expertise that only comes with time. - "We don't need a firewall, we have good host security" - no, you don't. If your network fabric is untrustworthy every single application that goes across the network is potentially a target. 3 words: Domain Naming System.
- "We don't need host security, we have a good firewall" - no, you don't. If your firewall lets traffic through to hosts behind it, then you need to worry about the host security of those systems.
- "Let's go production with it now and we can secure it later" - no, you won't. A better question to ask yourself is "If we don't have time to do it correctly now, will we have time to do it over once it's broken?" Sometimes, building a system that is in constant need of repair means you will spend years investing in turd polish because you were unwilling to spend days getting the job done right in the first place.
- "We can't stop the occasional problem" - yes, you can. Would you travel on commercial airliners if you thought that the aviation industry took this approach with your life? I didn't think so.
Goodbye and Good Luck
I've tried to keep this light-hearted, but my message is serious. Computer security is a field that has fallen far too deeply in love with the whizzbang-of-the-week and has forsaken common sense. Your job, as a security practitioner, is to question - if not outright challenge - the conventional wisdom and the status quo. After all, if the conventional wisdom was working, the rate of systems being compromised would be going down, wouldn't it?
source: http://www.ranum.com/security/computer_security/editorials/dumb/
Windows Vista product editions revealed
If you've been wondering why Windows Vista has taken a long time to reach Beta 1, we can now tell you why: there are seven separate editions of Vista headed your way. OK, that's not the reason for the delay, but how else do you introduce that many OS versions, without invoking Snow White & friends? Join me know as I romp through the various editions, many of which you'll see are just barely differentiated.
First up, there's Starter Edition, which like XP Starter Edition, is a crippled (and lame) product aimed at the two-thirds world. It will limit users to three concurrent applications, and provide only basic TCP/IP networking, and won't be suitable for most games. The next step up is Home Basic Edition, which is really the sibling to today's Windows XP Home. However, as the name suggests, there's also Home Premium Edition, and this is where we start to split features like hairs and create a gaggle of products. HPE will build on the the Basic Edition by adding, most notably, the next-generation of Media Center capabilities, including support for HDTV, DVD authoring, and even DVD ripping backed up (of course) by Windows DRM. For non-corporate types, this is probably going to be the OS that most people use. It's similar to XP Pro in power, but with all of the added bells and whistles for entertainment. Well, most of them.
Windows Vista Professional Edition won't occupy the same spot that XP Pro occupies today, because this time it's truly aimed at businesses. It won't feature the MCE functionality that Home Premium Edition has, but it begins to provide the kind of functionality you'd expect in a business environment, such as support for non-Microsoft networking protocols and Domain support. But don't expect too many businesses to necessarily turn to PE. Microsoft is also planning both a Small Business Edition and an Enterprise Edition, which build upon pro by adding (seemingly minor) features aimed at appealing to each market. SBE, for instance, includes a networked backup solution, while EE will include things like Virtual PC integration, and the ability to encrypt an entire volume of information.
Last but not least, there's Ultimate Edition. Hey, I'm just glad that they didn't call it Extreme Edition. I'll leave it to Paul Thurrott, who has all of the details, to explain (and promote) this beast:
The best operating system ever offered for a personal PC, optimized for the individual. Windows Vista Ultimate Edition is a superset of both Vista Home Premium and Vista Pro Edition, so it includes all of the features of both of those product versions, plus adds Game Performance Tweaker with integrated gaming experiences, a Podcast creation utility (under consideration, may be cut from product), and online "Club" services (exclusive access to music, movies, services and preferred customer care) and other offerings (also under consideration, may be cut from product). Microsoft is still investigating how to position its most impressive Windows release yet, and is looking into offering Ultimate Edition owners such services as extended A1 subscriptions, free music downloads, free movie downloads, Online Spotlight and entertainment software, preferred product support, and custom themes. There is nothing like Vista Ultimate Edition today. This version is aimed at high-end PC users and technology influencers, gamers, digital media enthusiasts, and students.
OK, everyone got that? There will be a quiz on Monday.
My initial reactions are reserved, because there's just not that much detail available. Pricing, for instance, would be really nice to know. Will Home Basic Edition debut below the price point of XP Home today? Place your bets. The one thing I will say is that I fear that this may cause a great deal of confusion on behalf of your average consumer. Two versions of XP were enough to cause confusion, and now Joe Blow has four choices that may fit the bill.
One final note worth mentioning is that this strategy does remove the "corporate Windows XP" option from the hands of pirates. Volume licensing for Pro, SBE, and EE may still mean that there will be copies of Windows Vista out there that don't "call home" for Windows Product Activation, but as you can see, Microsoft has removed most of the features that most pirates would want from those OSes. You won't see corporate licensing versions of Ultimate Edition.
source:http://arstechnica.com/news.ars/post/20050910-5298.html
Can Microsoft Out-Google Google?
For the past decade, Microsoft has largely ignored the Web as an emerging platform for application development with fears that it could render Windows obsolete. But that will all change next week, as Microsoft unveils a new strategy for transforming its Web properties into an open platform for developers.
The shift is a direct attack on Google, which has dominated the online space using that very same technique. Most of Google's offering, from its Search to Maps service to Desktop Sidebar all provide methods for third parties to extend -- and improve on -- the technologies.
This new development model, frequently referred to as Web 2.0, relies on modern Web standards and the wide adoption of broadband to facilitate almost instantaneous communication between a client and server. AJAX, or Asynchronous JavaScript and XML, has taken center stage as the programming language of choice for Web 2.0 applications.
As part of its new "Web platform" strategy, Microsoft will expose application programming interfaces, or APIs, for MSN Search using SOAP. Third party applications will be able to access up to 10,000 search results per day. Microsoft's Desktop Search API will also be opened up to outside developers.
Google and Yahoo have long offered access to their search APIs and both companies recently opened up their mapping services, which can be extended by developers for specific uses such as finding cheap gasoline or embedding directions into a Web site.
Microsoft is responding by giving developers free access to its MSN Virtual Earth service using JavaScript. MSN Messenger will also be opened up for companies to extend the communications service. For example, a company could create an add-on that automatically translates instant messages as they are sent.
Adam Sohn, a director in the marketing group at MSN, said on Thursday that Microsoft recognizes its platforms will have more value if more applications are built upon them. And the only way to encourage the development of such applications is to open up the technology to outsiders through APIs and other tools.
One of those tools, code-named "Atlas," will debut next week at Microsoft's Professional Developers Conference in Los Angeles. Microsoft will also discuss at the PDC ways developers can extend its new Start.com RSS aggregator.
At the core of Atlas lies the MSN Framework for building applications atop Microsoft's Web properties such as the next version of Hotmail and MSN Spaces. The object-oriented JavaScript framework will enable Microsoft developers to more quickly build features into MSN sites. Atlas will also closely be tied to ASP.NET 2.0 and Avalon, the presentation framework in Windows Vista.
But because many Web 2.0 applications reside in the Web browser, the underlying operating system essentially becomes irrelevant. That shift could pose a significant risk for Microsoft, analysts say, as the world becomes more connected and less reliant on desktop-only services.
Sohn, however, downplayed the risk to Microsoft's core Windows and Office businesses. He explained that Windows-based clients would be able to take advantage of the MSN platforms just as easily as those on the Web. Windows Vista, for example, will include native support for RSS and encourage the development of "connected" applications.
source: http://www.betanews.com/article/print/Can_Microsoft_OutGoogle_Google/1126286132
20 Things They Don't Want You to Know
Posted Thursday, August 25, 2005

Psssst! Wanna know a secret? How about a whole bunch of them? Sadly, the Colonel's Secret Recipe and Dick Cheney's Secure Undisclosed Location remain shrouded in mystery, but I'm going to spill the beans about a bunch of things that technology companies would rather you didn't know. These insider tips will help you cut through hype when you shop, save money when you buy, and get the most out of products you already own.

Here's a CPU manufacturing secret: Most CPUs can be overclocked to run at least a bit faster than usual, giving your PC a free speed boost. And on some rare occasions, low-end chips are capable of running just as fast as much more highly priced CPUs. But while overclocking can speed up your system, note that you must take care to properly cool your PC, or you might damage the CPU--and most system warranties won't cover that damage.
The big speed jumps usually come along when Intel or AMD has transitioned to a new manufacturing process and is getting great yields on even its high-end chips. When that happens, slower CPUs that use the same technology are ripe for overclocking. The classic example: Intel's Celeron 300A chip, a 300-MHz CPU that overclockers routinely ran at 450 MHz. Check in periodically with enthusiast sites like Anandtech (and HardOCP--they go wild when those situations arise.
To overclock most of today's CPUs, you bump up your computer's bus speed, either through the system's PC Setup (or BIOS) program or via a Windows-based utility such as NVidia's NTune. (See "Secret Tweaks" in our March 2005 issue.) Each time you increase the speed, you should use a utility like Motherboard Monitor to check the CPU's temperature while you stress the system by encoding video or playing a 3D game. If the core temperature rises above 60 degrees centigrade, or if you experience any system instability (crashes, corrupt graphics, etc.), roll back to the next-lowest setting and stay there.
Read more:
- You Never Have to Pay Full Price
- Faster Shipping Isn't Always Faster
- You Can Kill the Messenger
- Extended Warranties Aren't Worth It
- You Too Can Exploit Windows' Bad Security
- You Can Save Big Money on Big-Name Software Packages
- That Dead Pixel on Your LCD May Not Be Covered
- Your Cell Phone's Been Crippled
- High-End Manufacturers Don't Always Make Their Products
- You Can Call Amazon, EBay, and Other Web Businesses
- Security Center Can Be Muted
- Game Consoles Are Hackable
- You Can Use an IPod to Move Music
- You Can Get a Human on the Phone
- MP3 Players Run Down Too Fast
- Useless Specs
With so many ways to shop online, finding the best deal can be difficult--even at a major retailer such as Dell. The Bottom Line: If you're patient, or even just willing to look around, you should never have to pay full price for most tech products. Here are my favorite tips:
- When shopping at Dell, always check both the Home & Home Office and the Small Business sections. Prices for the same item often differ because independently operated business units manage these sections. Neither one consistently offers better deals, so when looking for specific items, check both areas periodically.
- If the product you're looking for isn't on sale, wait. Dell rotates promotional offers with blinding speed. Dell-branded products go on sale more often than items by other manufacturers do, but none of the products I tracked stayed at full price for longer than three weeks.
- The maximum discounts I've seen Dell offer--around 35 percent on its own items--are rare. But discounts of up to 20 percent on Dell-branded products and 10 percent on third-party items appear frequently.
- Deals on desktop and notebook PCs can be tough to evaluate, since Dell may also offer specials or free upgrades for included components (typically RAM, hard drives, and optical drives), making it difficult to calculate total savings on a system purchase. But sometimes you can find both discounts and free upgrades: In late July, for example, Dell offered a 34 percent discount on its XPS Gen 5 desktop, as well as a free upgrade from 512MB to 1GB of RAM.
- Check sites such as StealDeals.net and Techbargains.com (full disclosure: Techbargains powers PCWorld.com's Bargain Finder), which track day-to-day bargains on lots of shopping sites and which also list coupon codes that can augment the deals you find.
Not all deals are as good as they initially sound. Dell, for example, sometimes offers as much as $750 off notebooks that originally cost $1500 and up. But check the configuration and prices for notebook components carefully: Often the cost of adding RAM or a DVD burner will rise sharply during the deal period, cutting into your savings.
And before heading to a brick-and-mortar store, check the prices on its Web site at home, because local managers for chains such as Best Buy sometimes run in-store promotions that can produce prices different from those you'd see outside the store.
Everyone wants new books, CDs, and DVDs delivered yesterday. But for some folks, standard shipping may be just as fast as expensive two-day service. Try this experiment with a recent release you can stand to wait for. Use free or standard shipping, and check the package-tracking link to see what location handles the order (most of your orders probably ship from the same place). Most new releases I've ordered here in San Francisco ship from Reno or Fernley, Nevada--and they arrive in two days without expedited shipping.
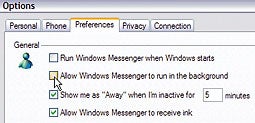
Know anyone who uses Windows Messenger as their instant messaging client? Me neither. Yet many of us have it sitting in our system tray anyway, because it often resurfaces even after you banish it using its own tools (select Tools, Options, click the Preferences tab, and uncheck 'Run Windows Messenger when Windows starts' and 'Allow Windows Messenger to run in the background'). You can, however, give Messenger the boot permanently; Click here for detailed instructions.

You know the drill: You're ready to pay for a new PC, HDTV, or peripheral, and take it home. But first you must suffer through your intrepid salesperson's 20-minute rap on why you'd be a fool to leave without buying an extended warranty. These plans are rarely a good deal.
Retailers push extended warranties hard because they're almost pure profit. By buying one, you're betting that your product will break, that the extended warranty will cover the damage, and that repairing the product would cost more than you paid for the extended warranty--an unlikely scenario. Extended warranties typically cost between 10 and 30 percent of a product's purchase price, so if these criteria don't hold true for one in every three to ten tech products you buy, routinely purchasing extended warranties will be a losing proposition for you.
Financial planners recommend making your purchase using a credit card that extends the manufacturer's warranty, and then putting the cost of the extended warranty into a repair or replacement fund. Often, by the time you need that money, you'll probably have saved enough to replace the nonworking tech product.
If you still want the extended service plan, read the fine print carefully; don't rely on the salesperson's assurances. Recognize that you're paying more for peace of mind (being prepared for the off chance something does go wrong) than service. And look for service plans that really do help. For example, some plans for rear-projection HDTVs cover the cost of replacing the backlight bulb, which you'll eventually have to do anyway.
My PC's firewall, antivirus scanner, spyware remover, pop-up blocker, and spam filter all agree: Windows is sorely lacking in PC security. That situation may not change until Windows Vista (formerly Longhorn) comes out sometime next year. Meanwhile here are a few ways to turn Windows' poor security to your advantage.
If you ever have to reinstall Windows, you'll need the license key that came with your copy. But that string of 25 random letters and numbers isn't always handy. You'd think that in a world where you can't use Windows without activating it, the code required to do so would be a well-guarded secret, but thanks to lax Windows security, a 252KB download--Magical Jelly Bean Software's free Keyfinder 1.41--will recover your license key in a snap. Just download and run the app, and write down your key. Now if only Keyfinder could find my Windows CD....
While your license key might be written down somewhere, your Web site passwords probably aren't. I've set Windows to remember a bunch of mine so that I don't have to figure out the right log-in and password every time I go to, say, Amazon.com. Still, my only record of the password is asterisked out on Amazon's site. Because Windows doesn't do much to secure those stored passwords, you can get them back using another download. Revelation 2 from Snadboy Software will reveal any asterisk-hidden passwords. (It's free, although the site asks for a donation if you keep the software.) A $15 utility called Aqua Deskperience pairs a similar password-revealing ability with some useful features such as a convenient screen grabber and the ability to copy text from any application (including those where a copy command isn't available).
Finally, if the password you've forgotten is your Windows XP administrator password--required for operations such as booting into Safe Mode--Microsoft has a knowledge base entry that will help you reset the password.
OEM: These three little letters, which stand for "original equipment manufacturer," can save you more than 50 percent on key software (see chart at left). Designed to accompany commercial systems, OEM editions have increasingly become available in stores such as Directron and Newegg. These stores are only supposed to sell OEM software with associated hardware--so for an operating system, you'd have to be buying parts for an entire PC. But most vendors let online stores sell OEM editions to anyone who buys a nonperipheral part--even a mouse, for example.
OEM software typically ships without a box, printed manuals, or the tech support you'd get with a retail version. But in return you save some serious coin.
Some monitor vendors are better than others when it comes to handling minor defects in their products. Any small anomaly in the manufacturing process can result in a dead or stuck pixel--a dot that stays bright or dark no matter what's being displayed. And since a typical 19-inch LCD has nearly 4 million tiny red, blue, and green subpixels, it's no surprise that some vendors balk at replacing a monitor if it has only a dead pixel or two.
But standards are improving. Philips's Perfect Panel guarantee and Asus's warranty for its V6V notebook display pledge replacements if even one pixel is dead.
Most vendors' LCD monitor warranties specify a minimum number of pixels that must be malfunctioning before they'll replace your display. Usually you can unearth a manufacturer's dead-pixel policy by searching its site for "dead pixels" or "pixel criteria." You might also find the policy in a PDF of the monitor's manual.
ViewSonic, for example, will replace a 14- to 15-inch monitor with more than four dead pixels; a 17- to 19-incher with seven dead pixels; and a 20-inch or greater monitor with more than ten stuck subpixels. Dell will replace monitors with six or more "fixed pixels"; NEC requires ten "missing dots." Most makers will also consider replacing a monitor that has a few dead pixels in a concentrated area.

To tether you to their service, carriers "lock" phones so you can't use them on a competitor's network. And sometimes carriers disable other features as well. But with a little time and effort (and spare change), you might be able to unlock your phone regardless of whether your carrier cooperates. Be aware, though, that doing so might invalidate your phone's warranty; read the fine print.
Why do carriers do this? Money. Service providers generally charge less for phones than third-party vendors do, and they need to recoup that money. So, for example, some carriers make it difficult for you to employ Bluetooth to let your phone act as a dial-up modem for a notebook or handheld (presumably to push you toward expensive over-the-air data services). Locked GSM phones also cost you money when traveling, as you can't swap out your SIM (Subscriber Identity Module, the tiny card that holds the phone number and other information specific to your handset) for one from a local carrier, which generally will charge less than most U.S. carriers do for overseas roaming.
The easiest and most common unlocking technique is to enter special numbers on the dial pad--typically an unlock code plus your handset's International Mobile Equipment Identifier (IMEI), Electronic Serial Number (ESN), or Master Subsidy Lock code (MSL). Some phones, including Samsung and Sony Ericsson models, you can unlock only by connecting them to a PC using special cables and software.
The safest way to get your unlock code is from your carrier. T-Mobile, for example, will provide codes 90 days after you subscribe. Cingular generally doesn't help customers unlock phones, but makes exceptions on a case-by-case basis, says spokesperson Ritch Blasi. Sprint won't unlock phones--period. (Verizon Wireless says its CDMA handsets are unlocked.)
If your carrier refuses to help, third parties will sell you unlock codes for about $30 and up; a Google search for "unlock phone" produces links to Bongo Wireless, GSM Locker, and Mobile Fun. Many of these outfits are Web-based, but independent brick-and-mortar shops are preferable because you can walk in and talk to a person if there's a problem. Whatever company you use, make sure it's legit: Find a contact number, and call a sales rep to get details such as cost and service guarantees. If the unlock code doesn't work, will you get your money back? What will the company do if the unlocking procedure breaks the phone?
A Google search will also lead you to forums and blogs where fellow cell phone users share unlocking secrets--for example, Howard Forums (registration required) and Treonauts, which provides unlocking tricks for Cingular's Palm Treo 650.
Some blog sites also help you circumvent restrictions on Bluetooth file transfers. For example, IrishEyes and RussellBeattie.com publish instructions on how to unleash some of the Bluetooth powers of Verizon's Motorola V710 handset.
It's tough to know who really makes anything these days. In an era of shrinking profit margins, major companies such as Dell and HP often save money by outsourcing much of the design and assembly of their products to a small number of less-well-known (and usually overseas) companies--sometimes the same companies that supply cut-price competitors.
For example, most vendors selling LCD monitors don't make their own LCD panels. Dell buys the panel in its 24-inch wide-screen 2405FPW from Samsung; HP gets the panel in its L2335 monitor from Philips. A handful of companies provide the basic engines for most CD and DVD recorders, as well.
Does this mean that, say, your NEC monitor is no better than the Brand X model made with the same panel, or that your Sony DVD burner is no different from a no-name burner made with the same optical-drive engine? Not necessarily. The answer depends mainly on the type of product you're buying.
With LCD monitors, for example, vendors have many ways to add features and enhance the overall quality of the product. A company like Dell or HP can afford to invest a lot more than a no-name outfit can in the industrial design, the physical adjustment options, and the user interface for tweaking the monitor's setup.
For more commoditized products--items such as optical drives, where the form factor is constrained and where prices have dropped so low that there's little profit margin for manufacturers to compete over--the big-name vendors don't have as great an advantage. Of course, there will still be important differences in various vendors' warranties, tech support, and software bundles; however, the performance of two products based on the same engine should be quite similar. In that case, you should be able to get good value by choosing a high-quality product regardless of the brand name, such as one of the top-performing, inexpensive drives on our Top 10 DVD Drives chart.
Sometimes the best e-mail and chat support in the world is no substitute for a conversation with a real person. But that kind of talk isn't cheap, so to cut costs, Net-based companies like Amazon often make their phone numbers hard to find. Not to worry: A site called Cliché Ideas has dug them up:
- Amazon: 800/201-7575
- EBay: 800/322-9266
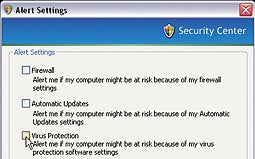
I keep my Windows system pretty well secured, but somehow that doesn't prevent Windows' Security Center from informing me that 'Your computer might be at risk' every morning when I turn on my computer. That message gets old fast. To banish it for good, go to Start, Control Panel, Security Center. Then click Change the way Security Center alerts me in the resources box and uncheck all of the boxes on the resulting screen.

Today's game consoles are powerful, crammed with useful technology, and (to habitual PC buyers) relatively inexpensive, so it's no surprise that hackers are constantly finding new ways to make them do more than just play games. The Xbox, for example, is essentially a PC with specialized graphics and audio hardware and a CPU that's a few generations old. With some dedicated hacking you can install Linux on it and use it as a PC. See Xbox Linux Project's step-by-step guide for answers to any questions you might have. (I did not find a similarly simple way to turn an Xbox into a Windows PC.)
Within a week of its release, Sony's PlayStation Portable had been hacked to let the user customize its background images and browse the Web using a secret browser built into the game Wipeout Pure. The PSP Hacks site has the story on this and other PSP hacks, including the continuing effort to allow the device to run home-brewed software. At press time Sony had just released a firmware upgrade that adds a Web browser and customizable background images, but locks out the latest home-brew hacks. Count on hackers to find a way around that eventually.
Apple doesn't make it easy to employ your IPod to duplicate your music collection on both your work and home PCs, but you can do it. If you have a Windows machine, simply plug in your IPod, find it listed in Windows Explorer, and make sure your machine can view hidden files.
Open the 'IPod_Control' folder and copy the 'My_Music' folder to your PC. Import those tracks into ITunes and put them in order there. Select Edit, Preferences, and choose the Advanced tab. Select a location for your music library by clicking the Change button, and then check Keep iTunes Music folder organized.
Utilities such as the $15 IPodRip--available for PCs and Macs from The Little App Factory--can help automate this process.
Follow the directions at Paul English's Find-A-Human IVR Phone System Shortcuts site to reach a human operator at any of more than 60 cell phone, PC, and travel firms.

Today's digital audio players and other portable devices often feature two levels of "off." One--a standby mode that allows the player to turn power back on quickly after a period of inactivity--keeps some of the player's circuits active and constantly draining a bit of power. That's what Jan Schuppius and several other members of Creative Labs' MP3 support forum found was reducing the battery life on their Zen Micro players from 12 hours to fewer than 6 hours. (Click here for their analysis.)
Creative fixed that problem in early July with a firmware update that lowered the standby time to 4 hours before the device shuts down fully, but I found the same drawback with an IRiver H10 I've been testing. Device manufacturers could follow Creative's lead in lowering standby time or correct this issue by permitting users to completely power down their players. Given the choice, many would opt for longer battery life.
Not all zoom is created equal. While optical zoom uses the camera's lens to increase magnification, digital zoom uses software built into a camera to magnify a subset of an image captured by a lens. The software does this by upsampling (or interpolating) pixels--generating new image data based on samples from the original pixels. That process can degrade the quality of the photo, making it blurry and pixelated. Optical zoom is the important number to look for.
An LCD's response time is supposed to tell you how well a monitor will respond to fast-moving images. Unfortunately, LCD manufacturers measure response times in so many different ways that the figures they quote are pretty much useless, as we found out in "LCD Specs: Not So Swift." And contrast ratios aren't much use either. In June 2003, we found monitors that underperformed their ratings by more than 50 percent.
Speaker manufacturers have a bag full of tricks they can use to inflate the power ratings of their speakers. But wattage should be pretty low on your list of deciding factors, especially for PC speakers. As any audiophile will tell you, there's no substitute for a good listening test when you're shopping for speakers. So put down the spec sheet, pick up a CD you're familiar with, and listen before you buy. If you insist on comparing speaker specs, look for a figure labeled Watts RMS that's broken down by channel instead of combined into a number representing total system power.
Hard-drive marketers like to push big numbers, such as a drive's burst transfer rate. But that number has little meaning. A typical Serial ATA drive can transfer bursts of data at 150 MBps when exclusively writing to or reading from its cache. But that doesn't happen often. A drive's sustained transfer rate or internal transfer rate (usually around 65 MBps), has more bearing on performance.
source: http://pcworld.com/resource/printable/article/0,aid,122094,00.asp







